Santa needs your help to investigate the Downdate vulnerability! He has a few urgent questions about it that he needs answered ASAP. Can you provide the answers to help keep the North Pole safe from these threats?
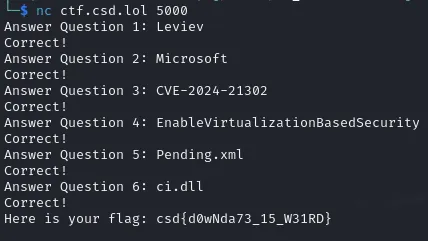
- What is the surname of the researcher who discovered the Downdate vulnerability.
- Which technology company is responsible for addressing the Downdate vulnerability?
- What is the CVE identifier associated with the Windows Downdate vulnerability?
- Which registry key is manipulated to disable Virtualization-Based Security (VBS) in the Windows Downdate exploit?
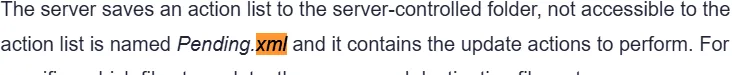
- What is the name of the XML file that the Windows Downdate exploit manipulates to control the update process?
- Which Windows kernel module is downgraded in the Windows Downdate proof-of-concept to exploit the "ItsNotASecurityBoundary" vulnerability?
Answer the questions with a single word @ nc ctf.csd.lol 5000