Agent Elf, Agent Elf, wake up! Elf Tim's computer has been compromised by malware from a rogue elf. This malicious elf has been secretly deleting critical files without anyone noticing—and it’s evident because Elf Tim's game in progress is missing. Can you recover the deleted files? Some of them are password-protected—can you retrieve those too?
long gone
Category
Points
Author
Forensics
75
qvipin
Solves (44)
| 1 | 12/04 4:05 pm | |
| 2 | 12/04 6:08 pm | |
| 3 | 12/04 6:14 pm | |
| 4 | 12/04 7:28 pm | |
| 5 | 12/04 10:22 pm | |
| 6 | 12/04 10:41 pm | |
| 7 | 12/04 10:52 pm | |
| 8 | 12/05 12:46 am | |
| 9 | 12/05 6:12 am | |
| 10 | 12/05 7:05 am | |
| 11 | 12/05 7:54 am | |
| 12 | 12/05 10:18 am | |
| 13 | 12/05 12:41 pm | |
| 14 | 12/05 12:44 pm | |
| 15 | 12/05 1:41 pm | |
| 16 | 12/05 5:08 pm | |
| 17 | 12/05 6:58 pm | |
| 18 | 12/06 3:36 pm | |
| 19 | 12/07 6:05 am | |
| 20 | 12/07 6:07 am | |
| 21 | 12/07 7:23 am | |
| 22 | 12/07 8:04 am | |
| 23 | 12/07 12:35 pm | |
| 24 | 12/08 12:38 am | |
| 25 | 12/09 3:33 pm | |
| 26 | 12/11 9:47 pm | |
| 27 | 12/12 3:42 am | |
| 28 | 12/16 7:47 am | |
| 29 | 12/16 12:17 pm | |
| 30 | 12/16 12:37 pm | |
| 31 | 12/17 3:23 pm | |
| 32 | 12/18 9:10 pm | |
| 33 | 12/19 11:01 am | |
| 34 | 12/20 8:47 am | |
| 35 | 12/21 12:10 am | |
| 36 | 12/21 6:36 am | |
| 37 | 12/22 1:10 am | |
| 38 | 12/25 7:30 am | |
| 39 | 12/25 10:46 am | |
| 40 | 12/25 5:22 pm | |
| 41 | 12/25 5:52 pm | |
| 42 | 12/25 7:14 pm | |
| 43 | 12/26 6:16 am | |
| 44 | 12/27 11:38 pm |
Submit flag
Write-up
Dharneesh's write-up was selected as the best write-up submitted for this challenge.
View this write-up on GitHubOpen the disk image in Autopsy but instead of choosing the data source as a disk image, chose unallocated space image file.
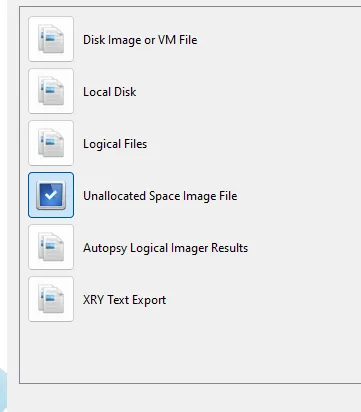
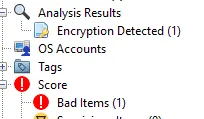
Run all the ingest modules on the image file, it should automatically do that when you load the disk image in. You’ll have to wait a while, but eventually, Autopsy finds a password-protected zip file. It is marked in bad items and in the encryption detected section.
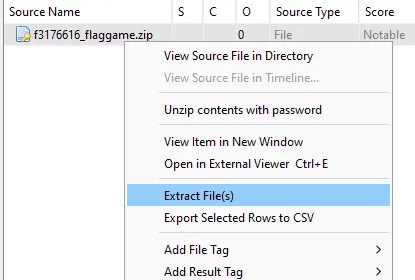
Once we see the file, we can right click and extract it.
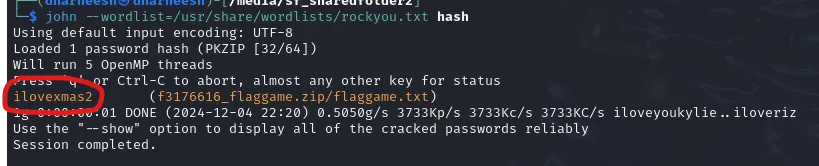
The next part is now to crack the password. Run zip2john ZIPFILENAME > hash and then run john --wordlist=/usr/share/wordlists/rockyou.txt hash to get the password.
Now just extract the zip file and view the text file inside of it to get the flag.
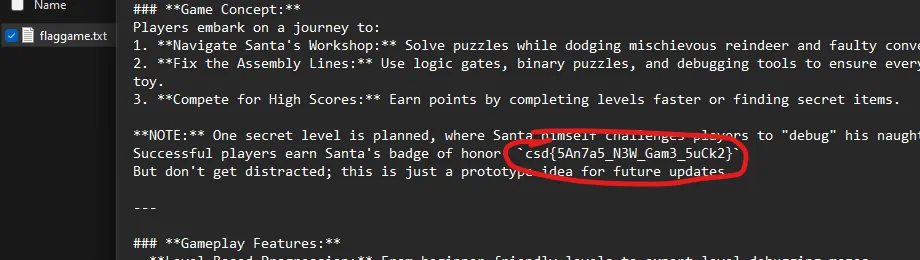
Flag: csd{5An7a5_N3W_Gam3_5uCk2}