This is a classic crackme. Figure out all the checks on the license key to create your own. When a successful key is detected it contacts a web url to grab your flag. If there are any web server errors DM ladderlogix on Discord.
Rusty Lock
Category
Points
Author
Reverse engineering
110
ladderlogic
Solves (31)
| 1 | 12/05 3:31 pm | |
| 2 | 12/05 4:01 pm | |
| 3 | 12/05 4:43 pm | |
| 4 | 12/05 6:16 pm | |
| 5 | 12/05 6:57 pm | |
| 6 | 12/05 7:16 pm | |
| 7 | 12/06 2:46 pm | |
| 8 | 12/06 5:07 pm | |
| 9 | 12/07 1:12 am | |
| 10 | 12/09 10:33 pm | |
| 11 | 12/10 7:52 am | |
| 12 | 12/10 1:47 pm | |
| 13 | 12/12 3:02 am | |
| 14 | 12/15 9:31 pm | |
| 15 | 12/16 3:44 am | |
| 16 | 12/16 10:43 am | |
| 17 | 12/17 3:54 pm | |
| 18 | 12/18 12:39 am | |
| 19 | 12/18 4:46 am | |
| 20 | 12/20 6:26 am | |
| 21 | 12/20 6:22 pm | |
| 22 | 12/23 7:59 am | |
| 23 | 12/23 5:41 pm | |
| 24 | 12/24 5:07 am | |
| 25 | 12/24 8:16 am | |
| 26 | 12/25 12:04 am | |
| 27 | 12/25 2:25 am | |
| 28 | 12/26 5:13 am | |
| 29 | 12/26 5:58 pm | |
| 30 | 12/27 11:14 am | |
| 31 | 12/31 2:58 pm |
Submit flag
Write-up
raul_26 (Fl4gged)'s write-up was selected as the best write-up submitted for this challenge.
View this write-up on GitHubStart by putting the binary and the pdb file in the same folder and open the exe file in binary ninja. The find the CrackMe::validate_password function and relabeled symbols to get an understanding of what is happening. There are 5 checks done:
- password length must be 12
- first digit must be even
- sum of the digits should be 69
- the password must contain a substring from the variable
pat, which is a substring of:YellowsGreenBlueRedOrangePurplesrc\\main.rs - last digit is odd
Here is the relabeled function in binary ninja:
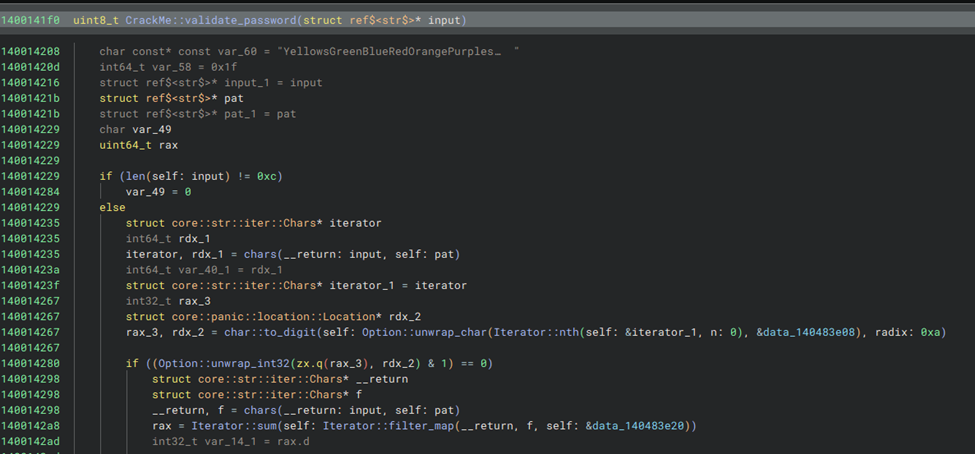
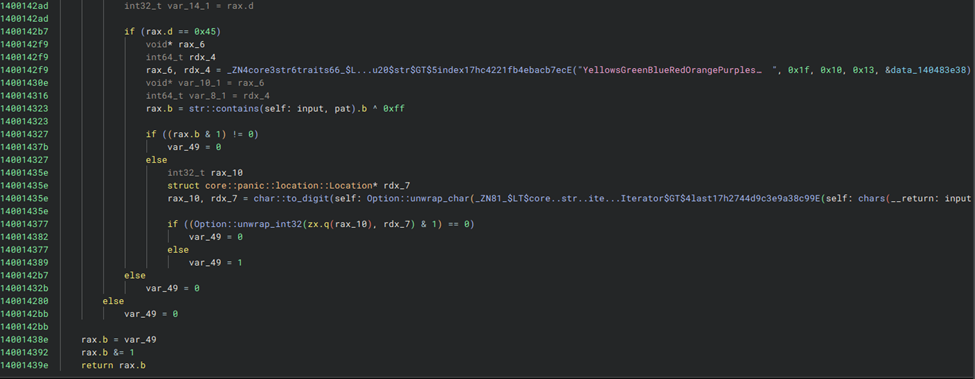
For the 4th condition, it is possible to find exactly which substring from pat must be included in the password, but I didn’t check the function in detail because it seems like a lot of work. I assumed there is some kind of slicing being done. Knowing this information, I just bruteforced the 4th condition. Ignoring that condition for now, I crafted this string: 8XXXX7999999, which respects the other four conditions. Now, I just replaced XXXX with a different substring of YellowsGreenBlueRedOrangePurplesrc\\main.rs until 8eRed7999999 gave the flag.
Flag: csd{V41id_L1ceNs3_K3y}